How to Detect Phishing Attacks
What is a Phishing Attack?
A phishing attack is an email or a text from a hacker who is trying to steal personal information for profit. Hackers will either encourage you to click on a link (which downloads malicious software onto your device), give them passwords or other sensitive data, or download a malicious attachment. Phishing, which originated in the 1990s, is one of the longest running, most dangerous cyber attacks. The term phishing is an analogy to fishing – a fisher throwing a baited hook into the ocean, hoping for a catch, is exactly like a hacker sending out phishing emails, hoping that a user will take the bait.
How to Detect Phishing Attacks
Examine the emails and texts you receive and ask yourself: do I know this person or company? Do I have an account with them? While you might think that spelling errors are a sign of a phishing email, it’s better to look for grammar errors and odd phrasing. While hackers may not have English as their first language, they’ll often use translation machines and spell check.
If there’s something that almost all phishing emails have in common, it’s a sense of urgency. Hackers may tell you, for example, that your account has been compromised. They may also make the email look like it comes from a program people that you rely on every day (such as Windows). Hackers know we lead busy lives, and the more critical they can make their message feel, the less time you have to realize that what you’ve received is a phishing email before it’s too late. If you have looked for the signs and you’re still unsure, contact the company or email sender by phone or through the live chat of a company’s website.
Phishing Email Example
Here is an example of a phishing email. Can you spot any of the signs?
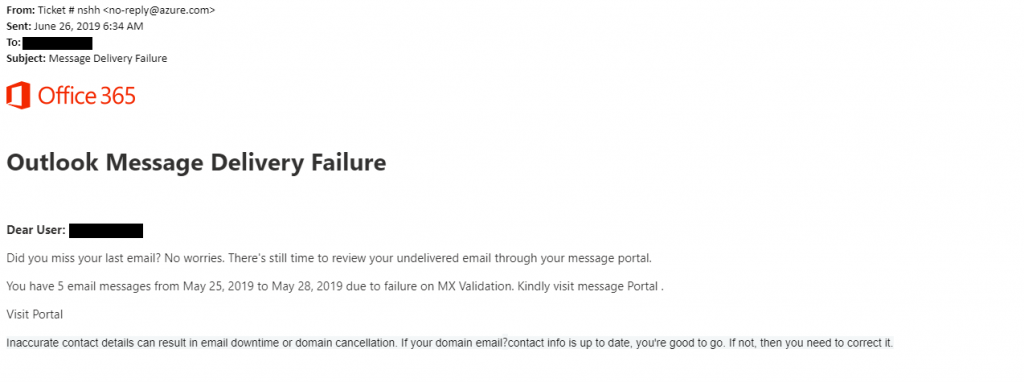
At first glance, this email may look like a legitimate Microsoft email because of the company logo. If you look closely, however, you’ll notice inconsistencies within the email which should not be there, because emails such as this are sent from a template that has been checked by the company’s copy editors. For example, you’ll notice there’s an extra space before the period at the end of the second paragraph, and the word portal is capitalized inconsistently. Also, emails from companies such as Microsoft will not address the recipient indirectly (Dear User) but will address them directly by name (Hi Bob).
How to Stop Phishing Emails
Your spam filters will catch most of the phishing emails that find their way into your inbox, but hackers continue to find clever ways of getting around them. Web filters will also catch some forms of phishing – check out our live stats page to see the number of phishing attacks we’ve found in the last 24 hours, along with the other types of threats we’ve detected. To help keep phishing attacks from happening on your device, make sure to keep your computer, phone, and anti-malware is up to date.
Types of Phishing
Hackers will try to cast a wide net or go for more specific targets. There are many different types of phishing, but the three most common types of phishing are deceptive phishing (which is the example covered in this blog), spear phishing, and whaling.
Spear phishing – Hackers will customize their emails with the targets name position, phone number, and other personal information. So, for example, hackers will find a target (using services such as LinkedIn) and send an employee from a company an email that looks like it’s from their manager, asking for a wire transfer on short notice.
Whaling – Hackers will try to go after the big fish, such as a CEO or members of a board, and steal their login credentials. Once they’re successful, they will use these login credentials to authorize fraudulent wire transfers to the banking institution of their choice.
What types of phishing emails have you seen? Let us know in the comments section below.
